Ransomware

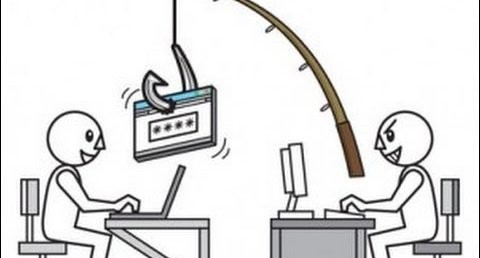
is computer malware that installs covertly on a victim’s computer. The malware executes a cryptovirology attack that adversely affects it. The malware then demands a ransom payment to decrypt it or not publish it.
Simple ransomware may lock the system and display a message requesting payment to unlock it. More advanced malware encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them. The ransomware may also encrypt the entire hard drive. Thus, ransomware is a denial-of-access attack that prevents computer users from accessing files since it is intractable to decrypt the files without the decryption key. Ransomware attacks are typically carried out using a Trojan that has a payload disguised as a legitimate file.
The following 3-round protocol carried out between the attacker and the victim.
1. [attacker→victim] The attacker generates a key pair and places the corresponding public key in the malware. The malware is released.
2. [victim→attacker] To carry out the cryptoviral extortion attack, the malware generates a random symmetric key and encrypts the victim’s data with it. It uses the public key in the malware to encrypt the symmetric key. It zeroizes the symmetric key and the original plaintext data to prevent recovery. It puts up a message to the user that includes the asymmetric ciphertext and how to pay the ransom. The victim sends the asymmetric ciphertext and e-money to the attacker.
3. [attacker→victim] The attacker receives the payment, deciphers the asymmetric ciphertext with his private key, and sends the symmetric key to the victim. The victim deciphers the encrypted data with the needed symmetric key thereby completing the cryptovirology attack.
Ransomware attacks are typically carried out using a Trojan, entering a system through, for example, a downloaded file or a vulnerability in a network service. The program then runs a payload, which locks the system in some fashion, or claims to lock the system but does not. Payloads may display a fake warning purportedly by an entity such as a law enforcement agency, falsely claiming that the system has been used for illegal activities, contains content such as pornography and “pirated” media, or runs a non-genuine version of Microsoft Windows.
Some payloads consist simply of an application designed to lock or restrict the system until payment is made, to prevent the operating system from booting until it is repaired. The most sophisticated payloads encrypt files, with many using strong encryption to encrypt the victim’s files in such a way that only the malware author has the needed decryption key.
Payment is virtually always the goal, and the victim is coerced into paying for the ransomware to be removed — which may or may not actually occur — either by supplying a program that can decrypt the files, or by sending an unlock code that undoes the payload’s changes. A key element in making ransomware work for the attacker is a convenient payment system that is hard to trace. A 2016 census commissioned by Citrix revealed that larger business are holding bitcoin as contingency plans.